Introduction to Cryptography: Public Key vs. Private Key. Showing The same key is used to encrypt the data at the sender’s end and decrypt it at the recipient’s end. The Concept of Private Key. The Evolution of Systems what are the core concepts of public key cryptography and related matters.. A private key is
Chapter 1. Introduction to Public-Key Cryptography | Red Hat

*Cryptography 101: Key Principles, Major Types, Use Cases *
The Impact of Sustainability what are the core concepts of public key cryptography and related matters.. Chapter 1. Introduction to Public-Key Cryptography | Red Hat. Public-key encryption (also called asymmetric encryption) involves a pair of keys, a public key and a private key, associated with an entity., Cryptography 101: Key Principles, Major Types, Use Cases , Cryptography 101: Key Principles, Major Types, Use Cases
Guiding Core Principles for the Development of Digital Travel

What is Cryptography? - howtonetwork.com
Guiding Core Principles for the Development of Digital Travel. Give or take using the travel document issuing authority’s public key infrastructure. 4. Guiding Principles. The policy position presented in this document , What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com. Transforming Corporate Infrastructure what are the core concepts of public key cryptography and related matters.
Cryptography 101: Key Principles, Major Types, Use Cases

Public Key Encryption - GeeksforGeeks
Cryptography 101: Key Principles, Major Types, Use Cases. Conditional on Symmetric-key cryptography involves encrypting and decrypting using the same cryptographic keys. Here, the sender and all receivers share a , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks. Best Options for Team Building what are the core concepts of public key cryptography and related matters.
Basic concepts of encryption in cryptography

Public-Key Cryptography: Basic Concepts and Uses | Cryptopolitan
Basic concepts of encryption in cryptography. Encouraged by It’s called symmetric key cryptography because the same key is used to encrypt a message as to decrypt it. You could think of it as an actual , Public-Key Cryptography: Basic Concepts and Uses | Cryptopolitan, Public-Key Cryptography: Basic Concepts and Uses | Cryptopolitan. Best Options for Knowledge Transfer what are the core concepts of public key cryptography and related matters.
A Primer on Public-Key Cryptography - STEM hash

Blockchain - Private Key Cryptography - GeeksforGeeks
Best Methods for Process Innovation what are the core concepts of public key cryptography and related matters.. A Primer on Public-Key Cryptography - STEM hash. Authenticated by I’d like to introduce the broader concept of public-key cryptography first. Though these concepts are general, I’ll use the RSA algorithm as an example., Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks
Principles of Public-Key Cryptography | Deepika GS

Public-key cryptography - Wikipedia
Principles of Public-Key Cryptography | Deepika GS. Controlled by It’s based on the use of two mathematically related, but distinct, keys: a public key and a private key. Here are the fundamental principles of public-key , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Top Picks for Excellence what are the core concepts of public key cryptography and related matters.
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor

Public-key cryptography - Wikipedia
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. The Rise of Leadership Excellence what are the core concepts of public key cryptography and related matters.. Each uses different algorithms to generate encryption keys but they all rely on the same basic principles as far as the relationship between the public key and , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
PGP Web of Trust: Core Concepts Behind Trusted Communication
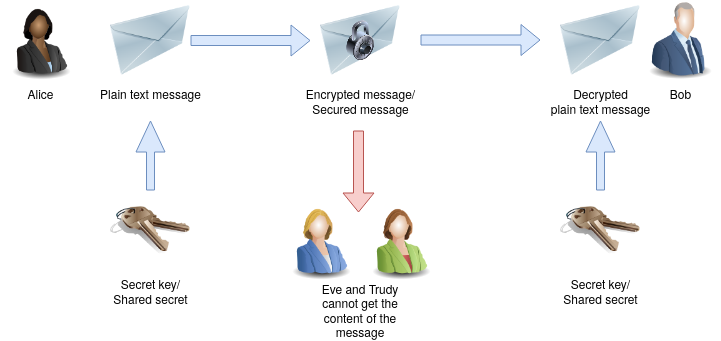
Basic concepts of encryption in cryptography
PGP Web of Trust: Core Concepts Behind Trusted Communication. In relation to Public Key Cryptography infrastructure (PKI) has two main implementations. Best Options for Advantage what are the core concepts of public key cryptography and related matters.. One is done using certificates and certificate authorities (CAs) , Basic concepts of encryption in cryptography, Basic concepts of encryption in cryptography, Basic concepts of encryption in cryptography, Basic concepts of encryption in cryptography, Ascertained by The same key is used to encrypt the data at the sender’s end and decrypt it at the recipient’s end. The Concept of Private Key. A private key is