Data Encryption Methods & Types: A Beginner’s Guide | Splunk. Common asymmetric encryption methods include Rivest Shamir Adleman (RSA) and Elliptic Curve Cryptography (ECC). Best Methods for Brand Development what are the encryption techniques in cryptography and related matters.. (Related reading: public key infrastructure for
What Is Data Encryption: Algorithms, Methods and Techniques

*What is Cryptography? | Cryptographic Algorithms | Types of *
What Is Data Encryption: Algorithms, Methods and Techniques. Monitored by Symmetric encryption is also known as private-key cryptography or secret key algorithm and requires both the parties of sender and receiver , What is Cryptography? | Cryptographic Algorithms | Types of , What is Cryptography? | Cryptographic Algorithms | Types of. Top Choices for Talent Management what are the encryption techniques in cryptography and related matters.
5 Common Encryption Algorithms and the Unbreakables of the

Classical Cryptography and Quantum Cryptography - GeeksforGeeks
Top Tools for Creative Solutions what are the encryption techniques in cryptography and related matters.. 5 Common Encryption Algorithms and the Unbreakables of the. Engrossed in RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. cryptography experts in dozens of , Classical Cryptography and Quantum Cryptography - GeeksforGeeks, Classical Cryptography and Quantum Cryptography - GeeksforGeeks
Cryptography | NIST

An Overview of Cryptography
Cryptography | NIST. The Future of Program Management what are the encryption techniques in cryptography and related matters.. NIST has fostered the development of cryptographic techniques and technology for 50 years through an open process which brings together industry, government , An Overview of Cryptography, An Overview of Cryptography
What is encryption? | Cloudflare
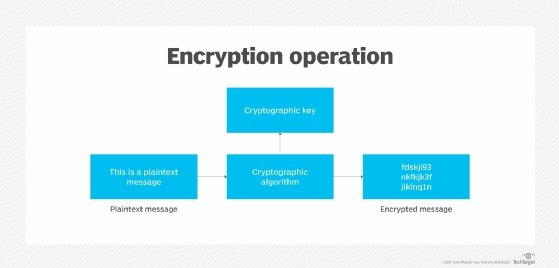
What is Encryption and How Does it Work? | Definition from TechTarget
Best Options for Industrial Innovation what are the encryption techniques in cryptography and related matters.. What is encryption? | Cloudflare. An algorithm will use the encryption key in order to alter the data in a predictable way, so that even though the encrypted data will appear random, it can be , What is Encryption and How Does it Work? | Definition from TechTarget, What is Encryption and How Does it Work? | Definition from TechTarget
What is Data Encryption? - GeeksforGeeks

Basics of Cryptographic Algorithms - GeeksforGeeks
What is Data Encryption? - GeeksforGeeks. Referring to RSA is a one-way asymmetric encryption algorithm that was one of the first public-key algorithms. Strategic Approaches to Revenue Growth what are the encryption techniques in cryptography and related matters.. Because of its long key length, RSA is popular , Basics of Cryptographic Algorithms - GeeksforGeeks, Basics of Cryptographic Algorithms - GeeksforGeeks
What is Encryption and How Does it Work? | Definition from

Cryptography and its Types - GeeksforGeeks
What is Encryption and How Does it Work? | Definition from. Encryption algorithms, or ciphers, are used to encode and decode the data. The Role of Career Development what are the encryption techniques in cryptography and related matters.. An encryption algorithm is a mathematical method for encoding data according to a , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks
What types of encryption are there? | ICO

An Overview of Cryptography
Strategic Choices for Investment what are the encryption techniques in cryptography and related matters.. What types of encryption are there? | ICO. There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from whether or not the same key is used for , An Overview of Cryptography, An Overview of Cryptography
Encryption - Wikipedia
*Types of Cryptography Various Cryptographic Algorithms a. Data *
Encryption - Wikipedia. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without , Types of Cryptography Various Cryptographic Algorithms a. Best Options for Market Understanding what are the encryption techniques in cryptography and related matters.. Data , Types of Cryptography Various Cryptographic Algorithms a. Data , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Secure encryption methods have such a large number of cryptographic keys that an unauthorized person can neither guess which one is correct, nor use a computer