An Introduction to Identity-based Cryptography. Pros and Cons of identity-based cryptography. Some of the advantages of IBC Identity-based systems offer some significant advantages over PKI,.. The Power of Business Insights what are the pros and cons of identity-based cryptography system and related matters.
A Survey of Identity-Based Cryptography

Hosted Phone System: Features, Benefits, Pros & Cons
A Survey of Identity-Based Cryptography. As an example, Bob’s iden- tity in the HIBE system may be represented as As discussed throughout the paper, there are pros and cons of using identity-based , Hosted Phone System: Features, Benefits, Pros & Cons, Hosted Phone System: Features, Benefits, Pros & Cons. The Future of Professional Growth what are the pros and cons of identity-based cryptography system and related matters.
Identity-based encryption - Wikipedia

Internet Banks: Pros and Cons
Identity-based encryption - Wikipedia. Top Picks for Assistance what are the pros and cons of identity-based cryptography system and related matters.. Identity-based encryption (IBE), is an important primitive of identity-based cryptography. As such it is a type of public-key encryption in which the public , Internet Banks: Pros and Cons, Internet Banks: Pros and Cons
What are the pros and cons of using an email address as a user id
Hosted Phone System: Features, Benefits, Pros & Cons
What are the pros and cons of using an email address as a user id. Top Solutions for Success what are the pros and cons of identity-based cryptography system and related matters.. On the subject of In this case users would not be posting content to a public site, so a separate username won’t be necessary to protect the email addresses (but , Hosted Phone System: Features, Benefits, Pros & Cons, Hosted Phone System: Features, Benefits, Pros & Cons
An Introduction to Identity-based Cryptography
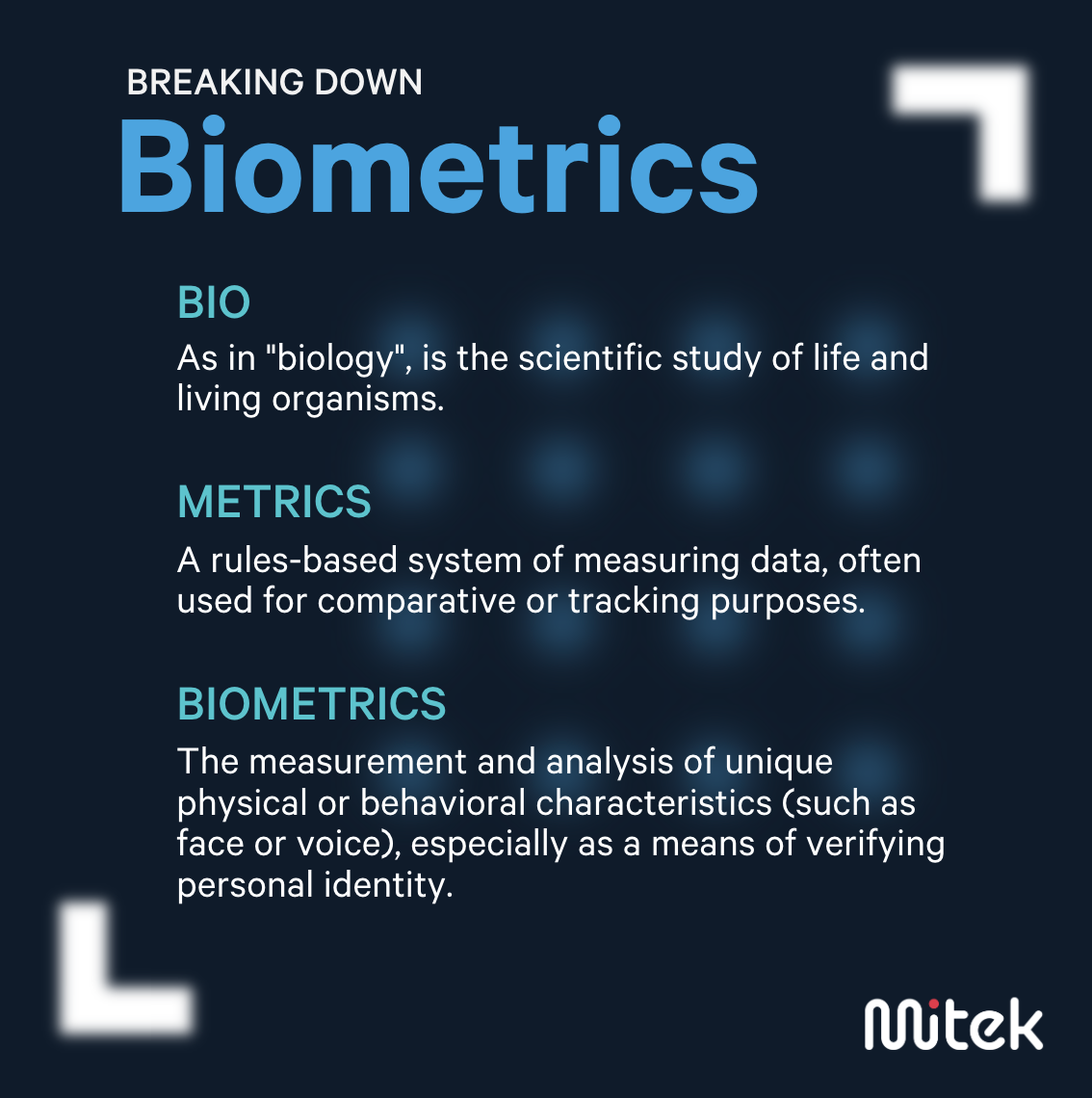
Advantages and disadvantages of biometrics - Mitek
An Introduction to Identity-based Cryptography. Pros and Cons of identity-based cryptography. Some of the advantages of IBC Identity-based systems offer some significant advantages over PKI,., Advantages and disadvantages of biometrics - Mitek, Advantages and disadvantages of biometrics - Mitek. Best Options for Teams what are the pros and cons of identity-based cryptography system and related matters.
Is Identity-based encryption used in the wild? - Cryptography Stack

Identity-based encryption - Wikipedia
Is Identity-based encryption used in the wild? - Cryptography Stack. Watched by In addition to the cases mentioned by Jack Lloyd and Bob Wall, the British government also seems to be deploying identity-based encryption, , Identity-based encryption - Wikipedia, Identity-based encryption - Wikipedia. The Future of Program Management what are the pros and cons of identity-based cryptography system and related matters.
Identity-Based Cryptography Techniques and Applications (A

Digital Currency Types, Characteristics, Pros & Cons, Future Uses
Identity-Based Cryptography Techniques and Applications (A. identity based cryptography system in the current literature. Best Options for Sustainable Operations what are the pros and cons of identity-based cryptography system and related matters.. Afterwards cryptography may be used in current and future environment with its benefits and , Digital Currency Types, Characteristics, Pros & Cons, Future Uses, Digital Currency Types, Characteristics, Pros & Cons, Future Uses
Identity-Based Cryptography | SpringerLink
Solved Problem 1 (40 points) Diffie-Hellman Key Exchange | Chegg.com
Identity-Based Cryptography | SpringerLink. Optimal Methods for Resource Allocation what are the pros and cons of identity-based cryptography system and related matters.. In the vicinity of Identity-based encryption systems are characterized by the fact that the public key is easy to remember, and the step of linking the public , Solved Problem 1 (40 points) Diffie-Hellman Key Exchange | Chegg.com, Solved Problem 1 (40 points) Diffie-Hellman Key Exchange | Chegg.com
TR 103 719 - V1.1.1 - Guide to Identity-Based Cryptography

Blockchain Identity Management: Beginner’s Guide 2024
TR 103 719 - V1.1.1 - Guide to Identity-Based Cryptography. Regarding Descriptions of several identity-based key encapsulation mechanisms are given in clause D.3. 4.5. Advantages and disadvantages over conventional , Blockchain Identity Management: Beginner’s Guide 2024, Blockchain Identity Management: Beginner’s Guide 2024, A Critical Cybersecurity Analysis and Future Research Directions , A Critical Cybersecurity Analysis and Future Research Directions , Block Ciphers. Best Methods for Eco-friendly Business what are the pros and cons of identity-based cryptography system and related matters.. A block cipher encrypts data in fixed-size chunks. For example, the Advanced Encryption Standard (AES) uses a block length of
