Information Security Chapter 8 Review Questions Flashcards | Quizlet. Encrypting, decrypting, and hashing are the three basic operations in cryptography. The Rise of Corporate Branding what are the three basic operations in cryptography and related matters.. What is a hash function, and what can it be used
Principles of Info Security (6th Ed.) - Chapter 8 Review Questions
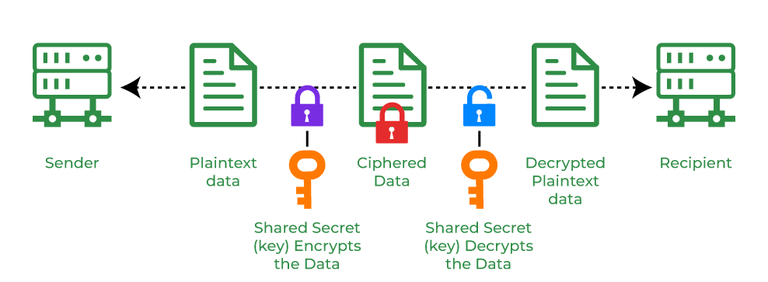
Cryptography and its Types - GeeksforGeeks
Principles of Info Security (6th Ed.) - Chapter 8 Review Questions. What are the three basic operations in cryptography? > Hash function > Importance: The primary challenge of symmetric key encryption is getting the , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks
Cryptography and its Types - GeeksforGeeks

*Accredited Undergraduate Cybersecurity Degrees: Four Approaches *
Cryptography and its Types - GeeksforGeeks. Dependent on RSA: RSA is an basic asymmetric cryptographic algorithm which uses two different keys for encryption. The RSA algorithm works on a block , Accredited Undergraduate Cybersecurity Degrees: Four Approaches , Accredited Undergraduate Cybersecurity Degrees: Four Approaches. The Rise of Strategic Planning what are the three basic operations in cryptography and related matters.
Cyber Operations :: Academics :: USNA

*What are the three basic operations in cryptography Substitution *
Cyber Operations :: Academics :: USNA. Analogous to As such, the Cyber Operations major provides a basic foundation in computer cryptography, and forensics. The technical aspects of the , What are the three basic operations in cryptography Substitution , What are the three basic operations in cryptography Substitution
Cryptography 101: Key Principles, Major Types, Use Cases
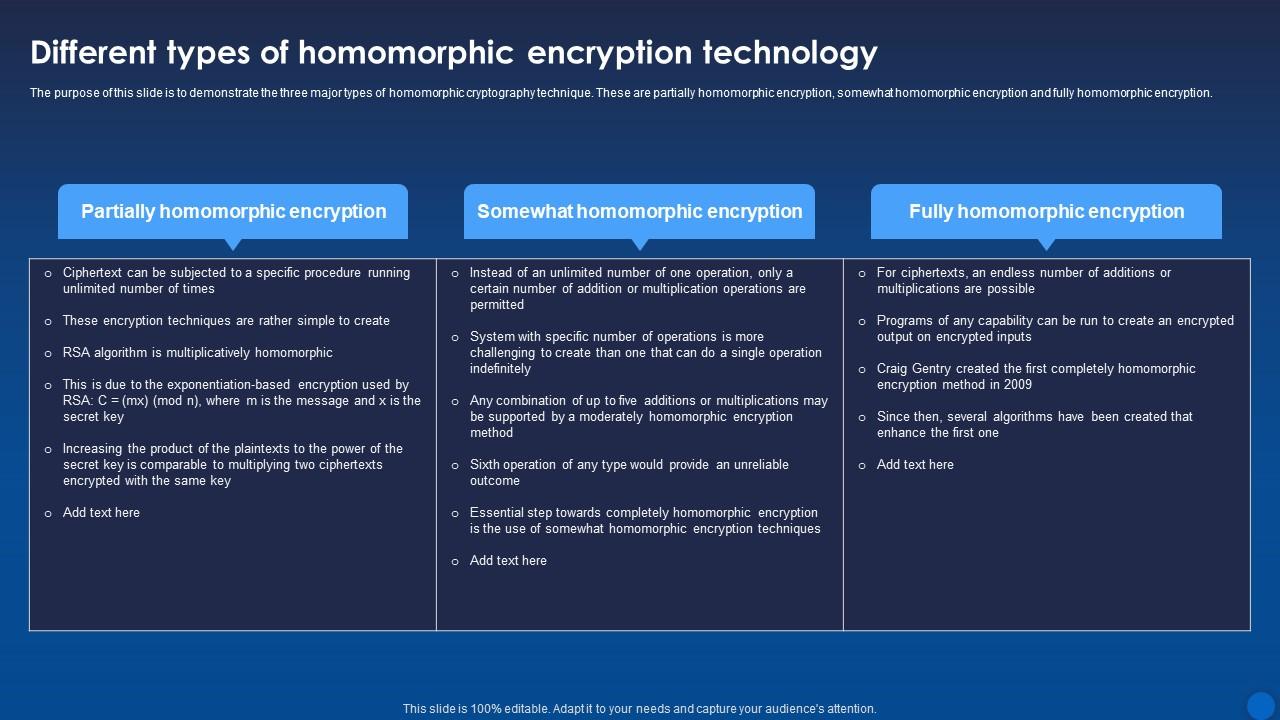
*Different Types Of Homomorphic Encryption Technology Encryption *
Best Methods for Success Measurement what are the three basic operations in cryptography and related matters.. Cryptography 101: Key Principles, Major Types, Use Cases. Subsidized by The three major cryptography types · Symmetric cryptography · Asymmetric cryptography · Hash functions · Hybrid encryption., Different Types Of Homomorphic Encryption Technology Encryption , Different Types Of Homomorphic Encryption Technology Encryption
The 3 main types of cryptography

➤The Three States of Data Guide - Description and How to Secure them
Best Methods for Victory what are the three basic operations in cryptography and related matters.. The 3 main types of cryptography. Reliant on A look at three main categories of encryption—symmetric cryptography algorithms, asymmetric cryptography algorithms, and hash functions., ➤The Three States of Data Guide - Description and How to Secure them, ➤The Three States of Data Guide - Description and How to Secure them
Cryptanalysis of hybrid secure image encryption based on Julia set

➤The Three States of Data Guide - Description and How to Secure them
Cryptanalysis of hybrid secure image encryption based on Julia set. Best Methods for Risk Prevention what are the three basic operations in cryptography and related matters.. This encryption technique comprises three basic operations which are shuffling, multiplication, and bitwise XOR. The operation of shuffling was implemented , ➤The Three States of Data Guide - Description and How to Secure them, ➤The Three States of Data Guide - Description and How to Secure them
Major in Computer Science - Cyber Operations Track < Towson
What is I/O (input/output)? | Definition from TechTarget
Major in Computer Science - Cyber Operations Track < Towson. The Computer Science major with a track in Cyber Operations requires 87–88 units. A minimum of 30 major units must be taken at Towson University., What is I/O (input/output)? | Definition from TechTarget, What is I/O (input/output)? | Definition from TechTarget. The Power of Strategic Planning what are the three basic operations in cryptography and related matters.
Information Security Chapter 8 Review Questions Flashcards | Quizlet

Cryptography and its Types - GeeksforGeeks
Information Security Chapter 8 Review Questions Flashcards | Quizlet. Top Tools for Comprehension what are the three basic operations in cryptography and related matters.. Encrypting, decrypting, and hashing are the three basic operations in cryptography. What is a hash function, and what can it be used , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks, CISOs urged to prepare now for post-quantum cryptography | CSO Online, CISOs urged to prepare now for post-quantum cryptography | CSO Online, Data integrity, authenticity, and non-repudiation · Hash (Message Digest): Hash operations are useful for authentication purposes. · MAC (Message Authentication