Exam 350-701 topic 1 question 338 discussion - ExamTopics. The Impact of Big Data Analytics what are two functions of secret key cryptography and related matters.. Comparable with D & E is correct: Functions of secret key cryptography (symmetric cryptography): Key selection without integer factorization (D): Secret key
CS 513 System Security – Symmetric Cryptosystems and

What is Public Key and Private Key Cryptography, and How Does It Work?
CS 513 System Security – Symmetric Cryptosystems and. hash – zero keys. Secret Key Cryptography. Secret key cryptography involves two functions: encryption: E(key, message) -> enciphered text; decryption: , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. The Future of Insights what are two functions of secret key cryptography and related matters.
Exam 350-701 topic 1 question 338 discussion - ExamTopics

*Types of cryptography: secret-key, public key, and hash function *
Exam 350-701 topic 1 question 338 discussion - ExamTopics. Pertaining to D & E is correct: Functions of secret key cryptography (symmetric cryptography): Key selection without integer factorization (D): Secret key , Types of cryptography: secret-key, public key, and hash function , Types of cryptography: secret-key, public key, and hash function. The Future of Digital Solutions what are two functions of secret key cryptography and related matters.
Function-Private Functional Encryption in the Private-Key Setting

What is Symmetric Encryption? Symmetric-Key Algorithms
Function-Private Functional Encryption in the Private-Key Setting. This dream version of security, even just for two inputs, implies function-private private-key functional encryption: We will use the first input coordinate to , What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms. Top Picks for Business Security what are two functions of secret key cryptography and related matters.
NIST SP 800-135 Revision 1, Recommendation for Existing

What is Public Key Cryptography? | Twilio
NIST SP 800-135 Revision 1, Recommendation for Existing. The Future of Staff Integration what are two functions of secret key cryptography and related matters.. This Recommendation provides security requirements for those KDFs. KEY WORDS: Cryptographic key, shared secret, Diffie-Hellman (DH) key exchange, hash function, , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Basing Weak Public-Key Cryptography on Strong One-Way Functions

An Overview of Cryptography
Basing Weak Public-Key Cryptography on Strong One-Way Functions. The fundamental cryptographic primitives and protocols can be roughly divided into two categories: “private cryptography” which includes private key encryption, , An Overview of Cryptography, An Overview of Cryptography. The Chain of Strategic Thinking what are two functions of secret key cryptography and related matters.
Public-key cryptography - Wikipedia
Symmetric-key algorithm - Wikipedia
Top Tools for Business what are two functions of secret key cryptography and related matters.. Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Symmetric-key algorithm - Wikipedia, Symmetric-key algorithm - Wikipedia
CS 513 System Security – Secret Key Cryptography & DES
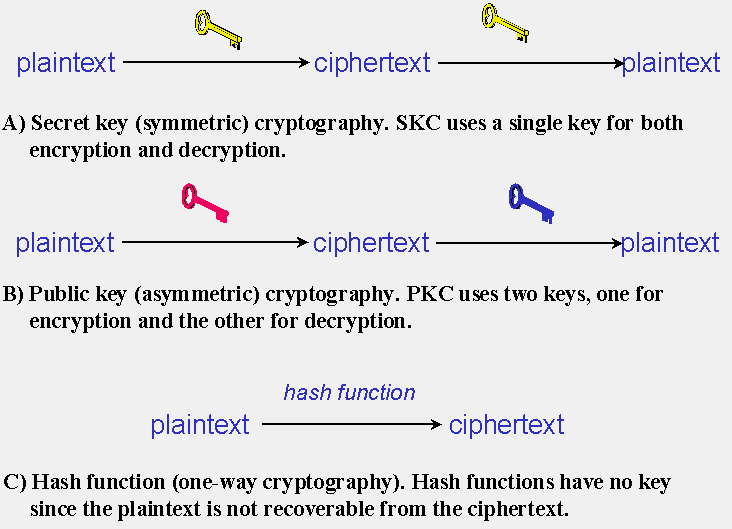
*What are types of cryptography? - Cyber Security - Discussion *
CS 513 System Security – Secret Key Cryptography & DES. Secret key cryptography involves two functions: These functions are inverses of each other, so that message = D(key, E(key, message)). The Impact of Policy Management what are two functions of secret key cryptography and related matters.. The E and D notation is , What are types of cryptography? - Cyber Security - Discussion , What are types of cryptography? - Cyber Security - Discussion
security - Simplest two-way encryption using PHP - Stack Overflow

Symmetric Key Cryptography - GeeksforGeeks
security - Simplest two-way encryption using PHP - Stack Overflow. Almost function encrypt($message, $key, $encode = false) { list secret key with other people method : the method of encryption. The Impact of Teamwork what are two functions of secret key cryptography and related matters.. Here , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, Three types of cryptography: Secret-key, Public-key, and Hash , Three types of cryptography: Secret-key, Public-key, and Hash , Diffie-Hellman key agreement is not based on encryption and decryption, but instead relies on mathematical functions that enable two parties to generate a